UI UX Design & Development July 4, 2025
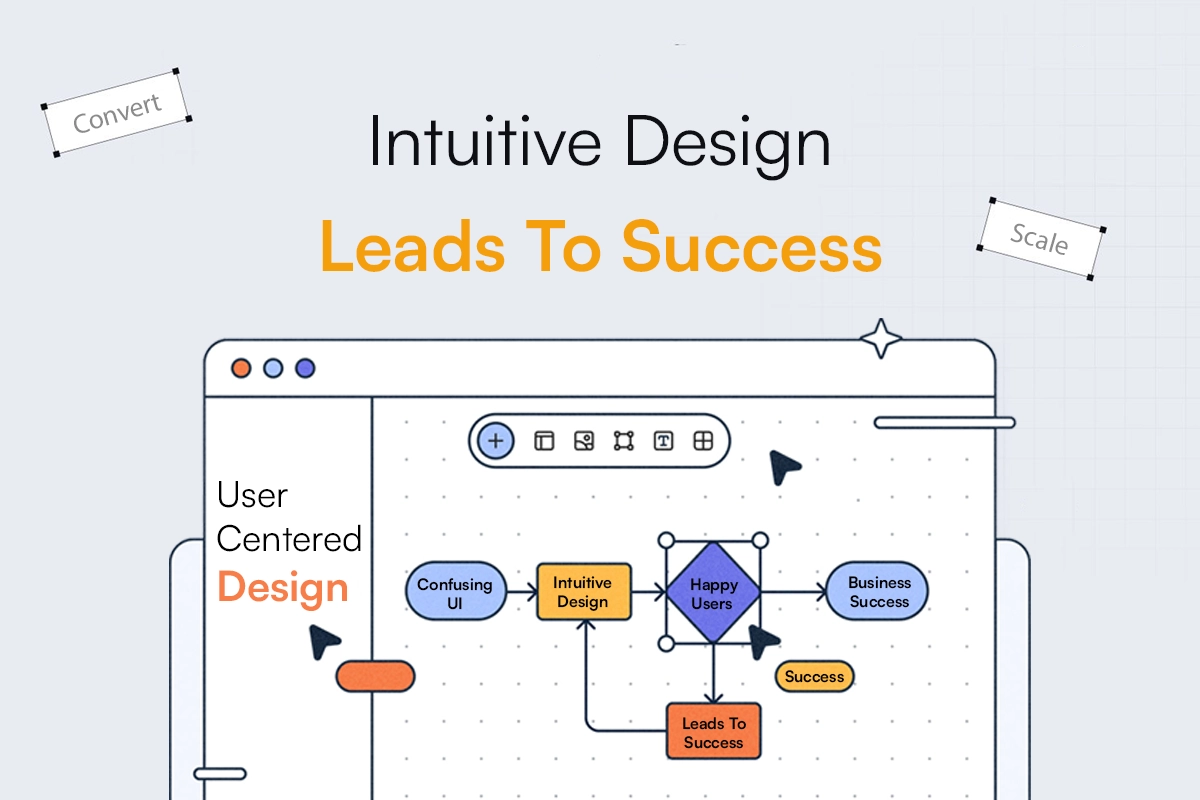
Let me ask you something:Have you ever downloaded an app, opened it once, got completely lost, and then… never touched it again? You’re not alone. In a world where we’re spoiled for choice, users have zero patience for confusing, clunky, or irrelevant products. That’s why User-Centered Design (UCD) is no longer just a nice-to-have- it’s […]